In case you haven’t heard, most EMC products are NOT susceptible to the HeartBleed SSL vulnerability. See the explanation and list in this KB article: OpenSSL Heartbeat Vulnerability (Heartbleed) in EMC products, https://support.emc.com/kb/185965.
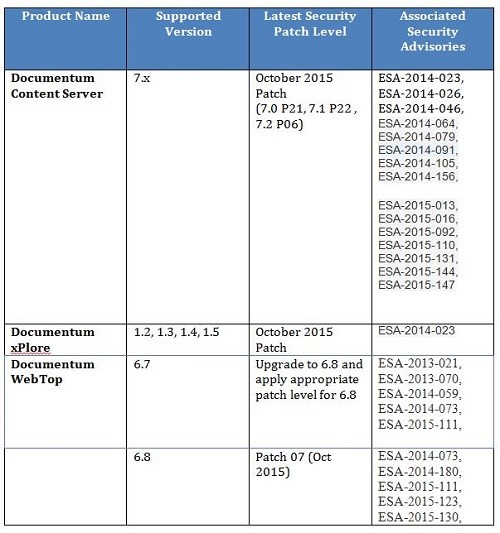
So, the two Documentum products listed, D2 and eRoom, say they are “Not Impacted”; however, the details state “In progress”. Does that mean testing is in progress, or a fix is in progress? And what about other Documentum products like Content Server, Java Method Server, Webtop, Business Process Engine, xPlore…? We already know that Syncplicity is affected, that ESA was issued yesterday, https://support.emc.com/kb/185966.
Stay tuned to the KB, EMC has promised updates.
UPDATE: EMC has updated the list of non-impacted products in this KB article to include a much larger collection of Documentum products; none of which use OpenSSL and therefore are not vulnerable.